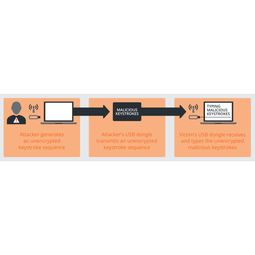
Overview
 |
Security Claims Evaluation |
Applicable Industries
Applicable Functions
Case Studies
Market Size
|
The Internet of Things (IoT) security market is expected to grow from USD 6.62 billion in 2017 to USD 29.02 billion by 2022, at a Compound Annual Growth Rate (CAGR) of 34.4%. Source: Markets and Markets |
Business Viewpoint
|
Risk Management: Businesses use security claims evaluation to assess the risks associated with their products, services, or systems. By evaluating security claims, businesses can identify potential vulnerabilities, threats, and compliance gaps that may pose risks to their operations, customers, or stakeholders. Compliance Assurance: Security claims evaluation helps businesses ensure compliance with industry standards, regulatory requirements, and contractual obligations related to security. By demonstrating adherence to security standards and best practices, businesses can build trust with customers, partners, and regulatory authorities. |
Stakeholder Viewpoint
|
Security Professionals: Security professionals are responsible for conducting security assessments, penetration testing, and vulnerability assessments to evaluate the effectiveness of security controls and safeguards. They provide expert insights and recommendations to improve security posture and mitigate risks. Regulatory Authorities: Regulatory authorities, such as government agencies, industry associations, and standards bodies, set guidelines, regulations, and compliance requirements related to security. They may require businesses to undergo security audits, certifications, or assessments to demonstrate compliance with applicable regulations. |
Technology Viewpoint
|
Security Assessment Tools: Security assessment tools, such as vulnerability scanners, penetration testing tools, security information and event management (SIEM) systems, and compliance management platforms, automate the process of evaluating security controls and identifying weaknesses. Blockchain Technology: Blockchain technology can be used to provide immutable records and tamper-proof audit trails, enhancing the integrity and trustworthiness of security claims and evidence.
|
Data Viewpoint
|
Security Metrics: Data-driven security metrics, such as vulnerability counts, patching status, incident response times, and security posture scores, help assess the effectiveness of security controls and measure improvements over time. Security Logs and Audit Trails: Security logs, audit trails, and event data provide visibility into security incidents, unauthorized access attempts, and system activities. Analyzing these logs helps identify security incidents, detect anomalies, and investigate breaches. |
Deployment Challenges
|
Security Assessment Methodologies: Organizations deploy security assessment methodologies, such as risk-based assessments, security audits, security testing, and compliance reviews, to evaluate security claims and identify vulnerabilities. Third-Party Assessors: Organizations may engage third-party security assessors, auditors, or consultants to conduct independent evaluations of security claims. Third-party assessments provide impartial evaluations and enhance credibility. |