
Published on 11/04/2016 | Operations
I don’t believe inaccessibility really exists today in the world of industrial automation and Controls system. My recommendation is to admit and plan for high integration with business systems, and to dismiss the idea, that control systems can be isolated.
If isolation is not an effective security measure, then how can you protect your control system then how can you help your company or clients deal with the conflicting requirements of more integration and more isolation?
As Stuxnet discovery on June 2010 showed us that there are multiple pathways to the control system, and they don’t require a connection to the Internet and demonstrated the vulnerability of these systems to cyber incidents
Any control system engineer integrating or commissioning automation technology in industries are well aware and know of the pressure on the operators, engineers form the management of industrial plants to increase efficiency and productivity, shrink the costs of the production and sharing the real time data / information across multiple industrial and enterprise systems. Today’s business pressures and the demand of sharing the data are growing with the fear of cyber-attack as the world has become aware that the Stuxnet worm was specifically intended to upset an industrial process.
Operators, engineers and the IT solution provider are under pressure to isolate automation systems at the same time as management is demanding for greater interconnectedness. In the present scenario of industries, control system plays a vital and key role in controlling and managing various services of industries which includes electricity, petroleum production, water, transportation, manufacturing, and communications. Vulnerability of these systems to cyber incidents can lead to various risks of safety, Environmental impact, loss of production, information theft and hampering the company image.
Threats to Industrial Control system: Threats to control systems can come from numerous sources, including adversarial sources such as attackers, bot-network operator, criminal groups, forging intelligence, insiders, phishers, spammers, industrial spy’s services and natural sources such as from system complexities, human errors and accidents, equipment failures and natural disasters. To protect against adversarial threats as well as known natural threats it is necessary to create a defense-in-depth strategy for the Industrial Control System .
Platform Software Vulnerabilities: Vulnerabilities in Industrial Control System can occur due to flaws, misconfiguration, or poor maintenance of their platforms, including hardware, operating systems, and Industrial Control System applications. These vulnerabilities can be mitigated through various security controls, such as OS and application patching, physical access control, and security software (e.g., antivirus software).
OLE for Process Control (OPC): Relies on Remote Procedure Call (RPC) and Distributed Component Object Model (DCOM) without updated patches, OPC is vulnerable to the known RPC/DCOM vulnerabilities.
Use of insecure industry-wide Industrial Control System protocols:Distributed Network Protocol (DNP) 3.0, Modbus, Profibus, and other protocols are common across several industries and protocol information is freely available. These protocols often have little or no security capabilities.
Buffer overflow: Software used to implement an Industrial Control System could be vulnerable to buffer overflows; adversaries could exploit these to perform various attacks.
Denial of service (DoS): Industrial Control System software could be vulnerable to DoS attacks, resulting in the prevention of authorized access to a system resource or delaying system operations and functions.
Unneeded services running: Many platforms have a wide variety of processor and network services defined to operate as a default. Unneeded services are seldom disabled and could be exploited.
Inadequate authentication and access control for configuration and programming software: Unauthorized access to configuration and programming software could provide the ability to corrupt a device.
The Source for Industrial Security Incidents (RISI1) is the world’s largest database of security Incidents in control and SCADA systems. An analysis of the data from 1982 to 2010 found that the type of incidents affecting control systems breaks down as follows: 1) 50% of occurrences were accidental in nature
2) 30% of occurrences were due to malware
3) 11% of happenings were due to external invaders
4) 9% of happenings were due to internal invaders
The ISA99 standards development committee brings together industrial cyber security experts from across the globe to develop ISA standards on industrial automation and control systems security. It identifies a wide range of security concepts, definitions, models, as well as a Process and guidance to develop cyber-security management systems for an IACS.
One way we can make the significant integration and improvements / isolation the control system, by Implementation of cyber security slandered model zone and conduit of ISA-99 security provides a framework for network security threats that arise from both the push for productivity, and preventing planned or unplanned prying in the Industrial automation & control system and its network and the fear of the next Son-of-stuxnet worm.
How Push for Productivity has degraded Control Network Security? The corporate networks have converged with Industrial Control System networks, there have been many integration projects where proprietary networks were replaced with commercial-off-the shelf equipment using Ethernet-TCP/IP technology.
This shift in technology has greatly increased the complexity and interconnectedness of control systems. Due to this shifts, now have many of the same vulnerabilities that have plagued enterprise networks. In addition, the controllers in the networks are now subjected to new threat sources that they were never designed to handle. The result has been a major increase in the number of plant disruptions and shut-downs due to cyber security issues in the control networks.
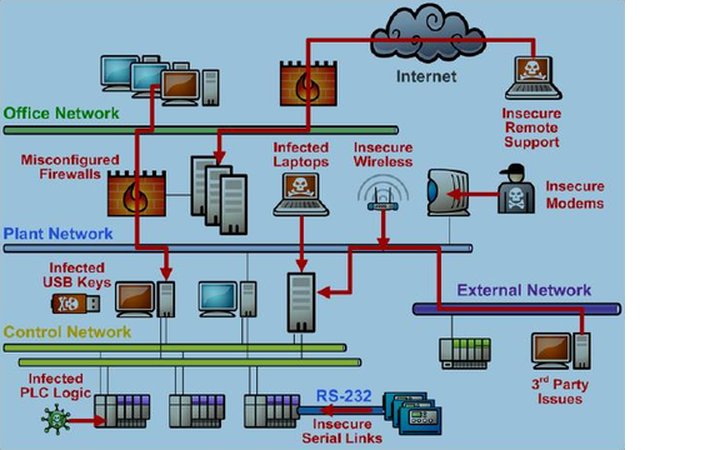
Increase in Soft Targets in plant floor: Supervisory Control and Data Acquisition and Industrial control System devices such as PLCs, DCS controllers, IEDs, and RTUs were designed considering the reliability and real-time I/O, but not for a secure networking. Many Industrial control system devices will crash if they receive malformed network traffic or even high loads of correctly-formed data. Also, Windows PCs in these networks often run for months at a time without security patches or antivirus updates, and are even vulnerable to outdated malware.
Numerous Openings of Entry in devices and network: Even without a direct connection to the Internet, modern control systems are accessed by numerous external sources. All of them a potential source of infection or attack these include:
1) Remote maintenance and diagnostics connections
2) Historian and Manufacturing Execution Systems (MES) servers shared with business users
3) Remote access modems
4) Serial connections
5) Wireless systems
6) Interfacing of mobile and laptops
7) USB devices
8) Data files (such as PDF documents or PLC project files)
Poor Internal Network Segmentation: Problems that originate in one part of the network can quickly spread to other areas which is happening in the real time in industries and in the cooperate network Ever than before the control system are now more complex than before comprising of hundreds or even thousands of individual devices installed in the plant floor. Unfortunately and unluckily the design of many of these networks has remained flat with virtually no segmentation.
Deploying of ISA99 zone & conduit security modules in an existing plant control system network: Proposing Implementation of zone and conduit models in the existing plant network is a tough decision for the plant management, engineers and operators, these phase is also challenging for the control system design engineer and commissioning engineer. For achieving the successful deployment of these modules, the first step is to plan when the actual deployment is to be done considering the maximum time frame to execute the program, on the other side it should not affect the production life cycle and throughput of the company then the revenue comes to the picture and consideration.
1) Dividing the exacting network in to 6 part as per the standard architecture OR
2) Converting the existing network section my section in terms of utility OR
3) Line by line in terms of production, conversation of the existing network as per OR
4) In full swing unit my unit OR
5) Running a new parallel deployments with the zone and conduit module and dividing the full plan in 6 level’s
Considering ISA99 zone and conduit security modules in a new phase of commissioning: Deploying the zone and conduit module with the network during the fresh phase of commissioning is very good and wise decision. The plant management and the control design engineer and commissioning engineer won’t have to phase many critical challenges during implementation
Zone and Conduit Security Model: The module theories of zones and conduit are a way to segment and isolate the various sub-systems in a control system network. A zone is defined as a grouping of logical or physical assets that share common security requirements based on factors such as critical and consequence. Equipment in a zone has a security level competence. If that competence level is not equal to or higher than the requirement level, then extra security measures, such as implementing additional technology or policies, must be taken.
Any communications between zones must be via a defined conduit. Conduits control access to zones, resist Denial of Service (DoS) attacks or the transfer of malware, shield other network systems and protect the reliability and privacy of network traffic. The controls on a conduit are planned to mitigate the difference between a zone’s security level capability and its security requirements. Concentrating on conduit mitigations which are typically far more cost effective than having to upgrade every device or computer in a zone to meet a requirement
If zone and conduit modules of ISA-99 are introduced in the network architectures of the control systems, this will provide a complete security life-cycle program for industrial automation and control systems. It consists of 11 standards and technical reports on the subject line
The good news is that engineers can address it by implementing good network architectures in their control systems. There is also limited opportunity for plant engineers to address the increase of soft targets in the short term
Conduit Delineation: The standard provides requirements based on a company’s assessment of its risk from cyber-attack. Since risk is a function of not only the possibility of a cyber-incident, but also the consequences of such an incident, the zones and conduits and the protection needed for each will vary for each facility. It is important to understand that ISA99 standards do not specify exactly how a company should define its zones or conduits.
Develop the network segmentation architecture: a network segmentation countermeasure strategy employing security zones shall be developed for IACS devices based upon the risk level of the IACS.
Employ isolation or segmentation on high-risk IAC Any high-risk IACS zone shall be either isolated from or employ a barrier device to separate it from other zones with different security policies, levels or risks. The barrier device shall be selected commensurate to the risk reduction required
Block non-essential communications with barrier devices Barrier devices shall block all non-essential communications in and out of the security zone containing critical control equipment.
Delineation of Security Zones: The control system security is defined in zone and conduit. Design starts with the facility or operation being analyzed to identify groups of devices that have common functionality and common security requirements. These groups are the zones that require protection. For e.g. A facility might first be divided into operational areas, such as materials storage, processing, finishing, etc. Then within these areas it could be further divided into functional layers, such as Manufacturing Execution Systems (MES), Supervisory Systems (i.e. operator HMIs), primary control systems (e.g. DCS Controllers, RTUs and PLCs) & safety systems line safety PLC.
Delineation of Security Conduits: Defining the security conduits in the pathways of the system through which data is passed between these zones these are the network conduits. Each conduit should be defined in terms of the zones it connects, the technologies it utilizes, the protocols it transports and any security features it needs to offer its connected zones. For determining the information transfer requirements between zones over the network is straight forward. Tools like traffic flow analyzers or even simple protocol analyzers can be used determining the hidden traffic flows. For example, are files ever moved via USB drive between the lab and the primary control systems, and any connection remotely connected to the RTUs using a dialup modem. These flows are easy to miss, but can result in serious security issues if not managed carefully. Data flow diagrams are an excellent tool to summarize the conduits and the traffic flows they contain. Each zone can be represented by a node and each flow can be represented by a vector.
How to secure the Conduits: There are two popular options once the conduits and their security requirements are defined, the final phase is to implement the appropriate security technologies by.
Deploying firewalls: These devices control and monitor traffic to and from a zone. They compare the traffic passing through to a predefined security policy, discarding messages that do not meet the policy’s requirements. Typically they will be configured to pass only the minimum traffic that is required for correct system operation, blocking all other unnecessary traffic. They can also filter out high risk traffic, such as programming commands or malformed messages that might be used by hackers to exploit a security hole in a product. Industrial firewalls are designed to be very engineer-friendly and are capable of detailed inspection of SCADA protocols such as DNP-3, Ethernet/IP and Modbus/TCP.
Installing VPNs (Virtual Private Networks): These are networks that are layered onto a more general network using encryption technology to ensure private transmission of data and commands. VPN sessions tunnel across a transport network in an encapsulated format, making them invisible to devices that don’t have the have access to the VPN members secret keys or certificates.
Deployment in zone and conduits ISA-99 with industries security application: There is the ideal platform on which to base frame an ISA-99 zones and conduits deployment. Any industrial security appliance should be plug and protect ready type, which is, as shipped from the factory, it obviously bridges all traffic between its Ethernet ports, so it can be installed in the control network without any changes to the design or IP addressing of the network. Some industrial security appliances can be fine-tuned for a particular purpose by installing firmware modules that implement security features, such as firewall, asset management, VPN and content inspection of particular protocols such as Modbus or OPC. In ISA-99 zones and conduits deployment, industrial security appliances can be installed in each conduit identified in the network. Once this is done, a firewall module can be activated in each appliance to provide the capability to filter all traffic passing through that conduit. The firewall makes it simple to build intrinsically secure networks because it automatically blocks and reports any traffic for which there is no allow rule. The control system engineer need only configure firewall.
A single security product, technology or solution cannot sufficiently protect an ICS by itself. A multiple layer strategy involving two or more different overlapping security mechanisms, a technique also known as defense-in-depth, is desired so that the impact of a failure in any one mechanism is minimized. A defense-in-depth architecture strategy includes the use of firewalls, the creation demilitarized zones, intrusion detection capabilities along with effective security policies, training programs and incident response mechanisms. In addition, an effective defense-in-depth strategy requires a thorough understanding of possible attack vectors on an ICS. These include:
1) Back-doors and holes in network perimeter
2) Vulnerabilities in common protocols
3) Attacks on Field Devices
4) Database Attacks
5) Communications hijacking and ‘Man-in-the-middle’ attacks
Selecting the technologies to secure the conduits and zones is the first stage of the zone and conduit security process. Some industrial security appliances are engineered specifically to support this defense in depth strategy in control networks. The whole zone and conduit approach implements a strategy of defense in depth multiple layers of defense distributed throughout the control network which has been proven in the IT community to be a strategy that works well.
"By introducing these new technologies in to control system which will contribute providing good improvements in plant performance, productivity and improve control network security and reliability. The standard framework of ISA 99 will provided companies to achieve and sustain security and throughout the life cycle, system integrators and control engineers who are playing the key role in the industries and who are expertise with segmenting of control networks for zones and conduits, will be able to mitigate cyber security threats that arise from both the push for productivity and Son-of-Stuxnet malware."