Overview
 |
Intrusion Detection Systems |
Applicable Industries
Applicable Functions
Case Studies
Market Size
|
The perimeter intrusion detection systems market was valued at USD 9.52 billion in 2017 and is projected to reach USD 21.75 billion by 2023, at a CAGR of 15.2% during the forecast period. Source: marketsandmarkets |
Business Viewpoint
|
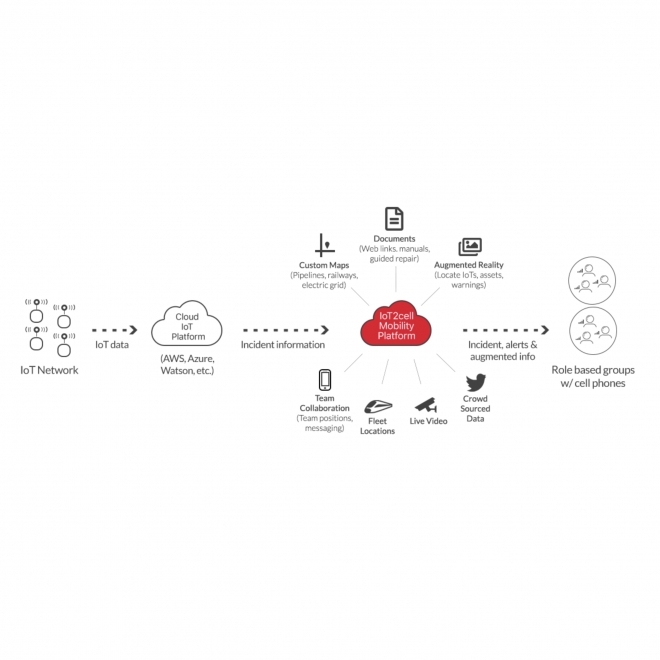
What value do Intrusion Detection systems provider to security professionals? Intrusion detection systems monitor network traffic in order to detect when an intrusion is being carried out by unauthorized entities. IDSes do this by providing some or all of the following functions: - Monitoring the operation of routers, firewalls, key management servers and files that are needed by other security controls aimed at detecting, preventing or recovering from cyber attacks. - Providing administrators a way to tune, organize and understand relevant operating system audit trails and other logs that are often otherwise difficult to track or parse - Providing a user-friendly interface so non-expert staff members can assist with managing system security - Including an extensive attack signature database against which information from the system can be matched - Recognizing and reporting when the IDS detects that data files have been altered - Generating an alarm and notifying that security has been breached - Reacting to intruders by blocking them or blocking the server What are the benefits of intrusion detection systems? They can offer organizations a number of benefits, starting with the ability to identify security incidents. An IDS can be used to help analyze the quantity and types of attacks, and organizations can use this information to change their security systems or implement more effective controls. It can also help companies identify bugs or problems with their network device configurations. These metrics can then be used to assess future risks. Moreover, it can also help the enterprises attain regulatory compliance and can also improve security response. Since IDS sensors can detect network hosts and devices, they can also be used to inspect data within the network packets, as well as identify the operating systems of services being used.
|
Stakeholder Viewpoint
|
IT Security Teams: IT security teams rely on IDS to monitor network traffic, detect security incidents, and investigate potential threats or vulnerabilities. They configure IDS rules, analyze security alerts, and collaborate with incident response teams to investigate and mitigate security breaches effectively, ensuring the confidentiality, integrity, and availability of business-critical information assets. Compliance Officers: Compliance officers leverage IDS to achieve regulatory compliance with industry standards, data protection regulations, and cybersecurity frameworks. IDS helps demonstrate due diligence in safeguarding sensitive data, maintaining audit trails, and reporting security incidents to regulatory authorities, ensuring adherence to legal requirements and industry best practices. |
Technology Viewpoint
|
What IDS types are the most common? IDS types range in scope from single computers to large networks. The most common classifications are: - Network intrusion detection systems (NIDS): it is a system that monitors these operating system files. - Host-based intrusion detection systems (HIDS): it is a system that analyzes incoming network traffic. Is there any other possibility to classify IDS by another approach? Yes, by detection approach. The most well-known variants are: -Signature-based detection: recognizing bad patterns, such as malware. - Anomaly-based detection: detecting deviations from a model of "good" traffic, which often relies on machine learning. There are also some IDS products that have the ability to respond to detected intrusions. Systems with response capabilities are typically referred to as an intrusion prevention system. What is the function of an intrusion detection system on a network? Intrusion detection is a passive technology; it detects and acknowledges a problem but interrupt the flow of network traffic.
|
Data Viewpoint
|
Network Traffic Analysis: IDS collects and analyzes network traffic data, including packet headers, payloads, and session metadata, to detect anomalous behavior, intrusion attempts, and malicious activities. By correlating network events and identifying patterns indicative of cyber threats, IDS generates security alerts and notifications to alert security teams of potential security incidents. Log File Monitoring: IDS monitors system logs, application logs, and security event logs generated by network devices, servers, and applications to identify unauthorized access attempts, privilege escalations, or suspicious user activities. By parsing log data, extracting relevant information, and correlating security events, IDS enables businesses to track user behavior, detect insider threats, and investigate security breaches effectively.
|
Deployment Challenges
|
What limitations can we find on these systems? - Noise can severely limit an intrusion detection system's effectiveness. Bad packets generated from software bugs, corrupt DNS data and local packets that escaped can create a significantly high false-alarm rate. - The number of real attacks is often so far below the number of false alarms that the real attacks are often missed and ignored. - A constantly changing library of signatures is needed to mitigate threats. Outdated signature databases can leave the IDS vulnerable to newer strategies. - For signature-based IDS, there will be a lag between a new threat discovery and its signature being applied to the IDS. During this lag time, the IDS will be unable to identify the threat. - It cannot compensate for weak identification and authentication mechanisms or for weaknesses in network protocols. When an attacker gains access due to weak authentication mechanisms then IDS cannot prevent the adversary from any malpractice. - Encrypted packets are not processed by most intrusion detection devices. Therefore, the encrypted packet can allow an intrusion to the network that is undiscovered until more significant network intrusions have occurred. - Intrusion detection software provides information based on the network address that is associated with the IP packet that is sent into the network. However, the address that is contained in the IP packet could be faked or scrambled. - Due to the nature of NIDS systems, and the need for them to analyze protocols as they are captured, NIDS systems can be susceptible to the same protocol-based attacks to which network hosts may be vulnerable. Invalid data and TCP/IP stack attacks may cause a NIDS to crash.
|