Published on 04/19/2016 | IoT Index
In terms of expectations, the Internet of Things (IoT) is on the crest of a hype wave.
Enterprises see the IoT as an integral part of the blueprint for evolving from the hardwired business models of today to the dynamic digitisation of the entire value chain. And among consumers ‘wearable’ adoption is rising rapidly.
However, significant advances in edge computing, networking, and big data analytics are still required for this truly disruptive technology to shape the future. Foremost amonst these is cyber security.
Security remains a major impediment. Methods to hack IoT technologies will depend both on whether security is built into the underlying technology and on implementation practices.
Worryingly, there are early indications that lessons learned through the development of cloud solutions over the past 20 years have often been ignored by manufacturers pushing into the new IoT market.
Risk exposure from IoT vectors is likely to remain low in the short-term for most enterprises due to the lack of complete connectivity. However, it is often higher than vendors realize. Due to the lack of universal standards and uncertainty regarding liability, many vendors view security as costly distraction from the race to enter the market.
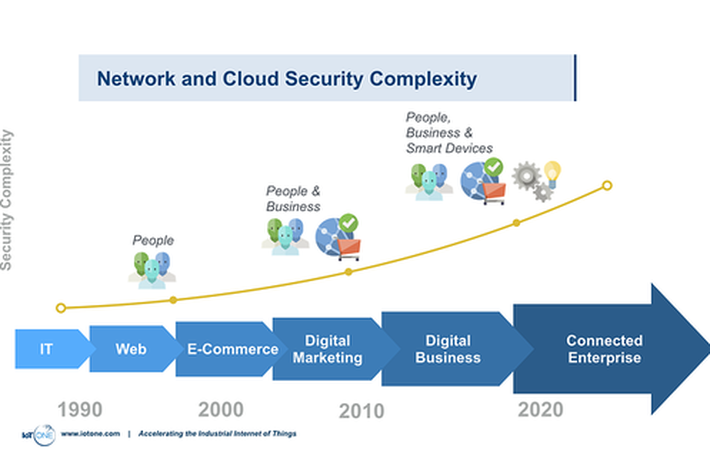
Risks will undoubtedly become more evident as adoption scales and lawsuits expose the true cost of weak security. The extension of shadow IT combined with the interconnectivity between home, office, and field devices means that security holes are already permeating corporate networks.
The concept of security by design must be given a higher priority by vendors as the IoT matures. Adopters likewise should properly budget security into IoT integration to offset the risk of adopting new technology in a loosely regulated environment.
The core principles of data, applications, networks, systems and hardware security remain applicable but complexity is an order of magnitude higher. The IoT will be a transformational, disrupting established value chains and market leaders. Yet it carries a spectrum of risks that affect more than just the IT department and must be addressed across the organization.