Published on 11/11/2016 | Strategy
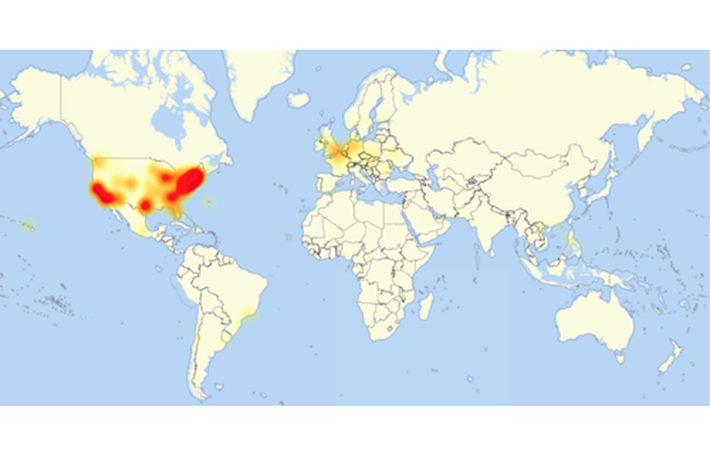
Cyber-attacks are not new to the internet community; the web admins, IT-Operations and security professionals and service providers – all have their guards up to prevent service disruptions and mitigate the aftereffects. Then why is everyone so shocked about the Friday attacks? What was so different about them? In simple terms – the scale and the source.
A distributed denial of service attack typically uses large networks of compromised servers or computers to send massive amount of false traffic to the sites, eventually overwhelming them and shutting them down.
In case of Friday’s attack, someone overwhelmed the DNS service provider Dyn. DNS service provider companies basically act as a bridge between the URLs you use on your browsers and the IP addresses associated with them. By targeting a DNS provider, the attackers could bring down end customers who use Dyn’s service. Dyn confirmed that the multi-wave attacks were carefully planned and executed and involved 10s of millions of IP addresses. Dyn also updated the internet community on mitigation plans by their operations and security teams.
The biggest concern with this particular attack was the source of the junk traffic – the so-called ‘Smart’ devices like Internet-enabled refrigerators, television, cameras, printers and other seemingly harmless household appliances. These devices were infested with Mirai botnet.
The malware Mirai manipulated vulnerable smart technology devices that were meekly protected by factory default usernames and passwords.
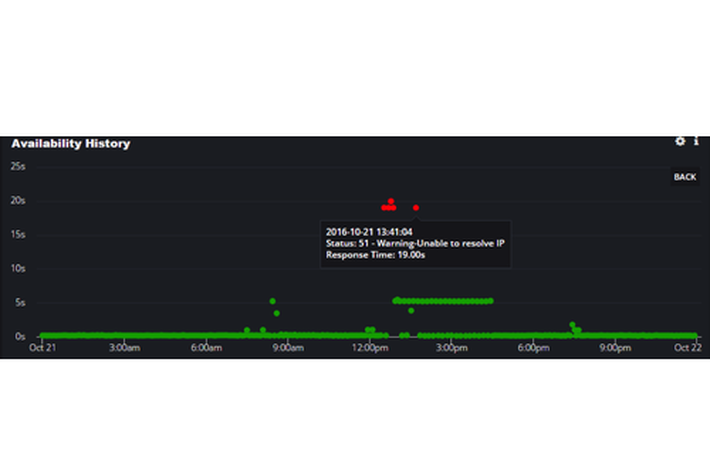
Advanced Synthetic Monitoring platforms like AlertSite cannot prevent such cyber-attack, but it can certainly give the web administrators and the IT-ops team a heads up within the first few minutes of the attack, so that they can take the necessary measures to keep the site from going down for an extended period of time. We saw spikes in DNS data for our customers and notified them about it on Friday.
Before these attacks, the Internet of Things seemed like a utopia of Smart living. Smart home, where every appliance and electronics device is connected and is operated on your fingertips, is a ‘dream come true’ for any modern consumer. However, security concerns seemed to take a back seat as brands kept romancing about the endless possibilities of IoT. We all have read many instances of IoT device being hacked from hundreds of miles away.
Forbes claims that there are hackers now selling and renting infected IoT devices to trigger future cyber-attacks. $4,600 can buy 50,000 bots and $7,500 can buy 100,000 of these malicious bots. The devices they choose as hosts for this malware are everywhere, and are vulnerable to security breaches with default vendor defined ‘factory default’ passwords like 1111 or 1234. This means that the attacker can easily build up a vast swarm of such spiked devices and send great volumes of traffic towards international targets.
Attacks like these stir up discussion around the root cause of such attacks as well as the prescriptive, predictive and preventive technologies and tools. Organizations can use this opportunity to educate themselves on the topic and remove vulnerabilities, if any. We encourage the users of smart devices – you and I – to understand the vulnerabilities, security measures and impact of such attack. So please update your usernames and passwords from admin/admin, take password security seriously and keep these smart machines as up to date as possible. Cyber-attacks affect all of us in one way or another and we are in this together.
Original article can be found here.