Published on 01/10/2017 | IoT Index
Whistleblower... snitch... stoolie... narc... canary... life has never been easy for those who report misdeeds. Financial, physical and social repercussions keep most people silent, be they corporate accountants or small town gangsters. Your connected devices, however, are not easily intimidated.
As your homes, offices and factories become increasingly connected, your devices and the clouds that serve them will know all of your dirty secrets. When a man recently turned up dead in his friend's hot tub the Arkansas police obtained a search warrant for an Amazon Echo and several connected devices. It was the water meter that snitched. Its data showed that 140 gallons of water were used between 1am and 3am, leading prosecutors to allege that the defendant used his garden hose to wash the patio clean of blood.
While the police need to apply for a warrant to seize your data and devices, hackers simply need to outsmart your systems. Recent events suggest that the hackers have the easier job.
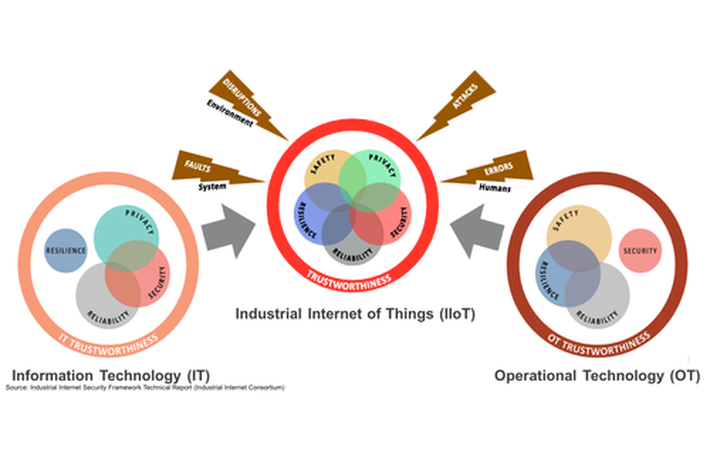
A 2016 report by Cybersecurity Ventures projects cybercrime damage to hit $6 trillion annually by 2021. President Obama declared the issue a national emergency. And the Industrial Internet Consortium published a 173 page Industrial Internet Security Framework last September to kickstart the discussion of practical solutions. The framework calls attention to the unique challenges that the marriage of IT and OT bring to the IoT.
CSC points to a projected 4,300% increase in annual data generation by 2020 as the main source of opportunity and concern. Your work and life can now be recorded in excruciating detail, from your conversations, to the frequency of your trips to the restroom, to the operational metrics of your assets. While I presume none of you are hiding dead bodies in your hot tubs, we are all accustomed to a high degree of anonymity that is soon to be extinct.
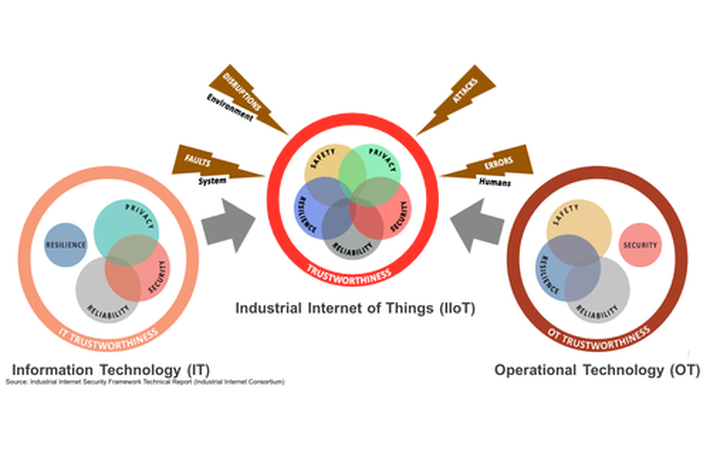
Business leaders from every industry are excited at the opportunities presented by a connected world. Unfortunately, perhaps none are more enthusiastic than cyber criminals. Hacks have been a costly nuisance. But now physical assets from trains to power plants to pacemakers are entering the game.
To be fair, exotic hacks receive excessive media coverage. Physical infrastructure security is boring but likely more important. Many businesses view cyber and physical security as separate challenges but Entrust points out that, "a top-tier cybersecurity plan [encompasses] physical protection". After all, many cyber breaches are enabled by a physical breach.
In 2015, the US Health and Human Services found that only 23% of data breaches involved remotely hacking IT systems. A further 34% were physical access breaches (imagine a consultant downloading your CRM into a USB drive). And 27% were done the old fashioned way, but simply stealing documents or devices (KISS).
The Global Cybersecurity Index ranked the US first in cybersecurity readiness. How much does first place cost? $19 billion is allocated to cybersecurity staffing and technology modernisation in the 2017 federal budget proposal.
As expected, the US also has the highest number of security vendors with 105 of the 238 cyber and physical security vendors that IoT ONE tracks.
If you need support addressing a security challenge, send a brief description to team@iotone.com and we'll refer 3-5 companies with relevant solutions.
In the first quarter of 2016, cyber-criminals extorted businesses for $209 million of ransom. In a typical case the Hollywood Presbyterian Medical Center paid US$17,000 to hackers who encrypted their files using ransomware. Shortly thereafter, MongoDB databases saw another variation of ransomware that exported users' content and required a Bitcoin transfer to return the data.
The question then is "To pay or not to pay?" Remember - extortion is a market governed by supply (ability to extort) and demand (willingness to pay ransom). Organizations that pay reduce their burden but increase the profitability of suppliers (hackers). Organizations that refuse to pay heroically eat the entire cost but disincentivize suppliers.
Sometimes you just can't win. In a recent attack, ProtonMail, a Switzerland-based encrypted email service, paid a ransom to a group that crippled their network with DDoS attacks. To their horror, a second group identified them as an easy mark and attacked the company.
The true cost of data breaches are not easy to define. Bruce Schneier estimates that the monetary cost of a cyberattack typically accounts for 0.4% of a company's annual revenues, far less than the estimated 5% lost to billing fraud. On the other hand, the British insurance company Lloyd estimates that cyber attacks cost as much as $400 billion a year when disruption to business operations are factored in.
Conclusion: Ransomware is a unique tragedy of the commons. Collectively refusing to pay would put extortionists out of business. But every company has an incentive to pay quickly and resume operations. My bet? This will remain a profitable market. Know any good ransomware startups looking for a seed investment?
Blockchain Tech Could Reinvent The Auto Industry
- Mahbubul Alam, Marketing Director, Movimento Group
While blockchain has been called revolutionary, people continue to view it as a financial technology. But blockchain could have a profound impact on people and devices in the modern world, including the vehicle sector.
IoT Solving Water Scarcity Issues
- Keith Robinson, Market researcher, City of Atlanta
IoT is helping to solve the water issues facing dozens of countries. Common uses include leak detection and monitoring water quality, water levels, flow and pressure of water. The impact could be pronounced due to the scale of waste and inefficiency.
- Bill Montgomery, CEO, Connect in Private
Physically Unclonable Function (PUF) generates a unique identifier by exploiting random physical factors introduced in the semiconductor manufacturing process, making it impossible to clone
NI partners with IBM and SparkCognition
NI, IBM and SparkCognition have announced a collaboration to increase the efficiency of industrial machinery using a combination of Industrial Internet of Things (IIoT) and machine learning. This new collaboration aims to provide software that can predict component failures before they occur, identify suboptimal operating conditions, and assist with root-cause analysis.
"With IIoT technologies driving vast sensitisation of industrial equipment, and massive amounts of data being collected on these assets, the collaboration between NI and SparkCognition powers the complex and intelligent processing of information to produce valuable insights," said Stuart Gillen, director of business development at SparkCognition.
Link Labs Certifies IoT LTE Cat M1 End Device on Verizon's 4G LTE Network
Link Labs, a leading innovator in low-power, wide-area network technologies that power the Internet of Things, has received certification for its low-power LTE Cat-M1 Sensor Suite for the Verizon 4G LTE Network, the world’s first commercial deployment of this breakthrough technology. The Link Labs Sensor Suite utilizes the Sequans Monarch chipset and is available as both a pre-certified device for OEM systems, as well as part of the fully-integrated Sensor Suite that Link Labs is launching in conjunction with Verizon’s LTE Cat M1 network roll-out, scheduled to reach nationwide coverage by the end of Q1 2017.
“Link Labs is proud to launch the first carrier-certified LTE Cat-M1 sensor device on the Verizon network, which will be the largest LTE Cat-M1 network in the US once fully deployed across the United States, scheduled for end of Q1 2017,” said Link Labs CEO, Bob Proctor. “Verizon and Sequans are truly at the forefront of the Internet of Things, and have been incredible collaborators across all aspects of the business. The ability to launch a battery-powered IoT application wherever there is Verizon LTE coverage is truly game changing for our customers.”
Patton launches new Power-over-Ethernet tool
Patton Electronics, a leading US manufacturer of UC, cloud, and IoT enabling solutions for carrier, enterprise and industrial networks, has started shipping its new CopperLink 1101 series of Power-over-Ethernet (PoE) Ethernet Extenders.
Copper network infrastructure is ubiquitous: most sites have twisted pair or coaxial cabling that was installed decades ago and still works. By leveraging the installed copper cable plant, Patton’s PoE Extenders prevent the disruption, delay and expense AC power construction or new CAT5e cable installation.
Standard PoE specifies 4-wire cabling, yet the CL1101 operates over two wires. By leveraging low-voltage copper infrastructure to deliver power the CL1101 eliminates the expense of a high-voltage construction project while enabling All-IP migration and the Internet of Things (IoT).
Nasscom, Georgia Tech to collaborate on innovation in IoT
In order to encourage innovation in internet of things, software industry body Nasscom’s Centre of Excellence for IoT and Georgia Tech Advanced Research (GTARC) have signed an agreement for advancing internet of things (IoT).
GTARC provides contracting, grant, and research administration services for the Georgia Tech Research Institute (GTRI), while Nasscom’s CoE-IoT is engaged in building talent, supporting startups and creating applications for some of India’s key projects such as smart cities, smart health, smart manufacturing and smart agriculture.
The two will work and share information across a variety of sectors — from industrial, healthcare, agriculture and smart homes, and the use of IoT to improve productivity with reduced natural resource use. Georgia Tech focuses on emerging technologies and Nasscom hopes both will mutually benefit from the partnership.